Vault 部署教程
AI-摘要
切换
Tianli GPT
AI初始化中...
介绍自己
生成本文简介
推荐相关文章
前往主页
前往tianli博客
安装 Vault
Windows 环境
- 下载 Vault 的 Windows 二进制文件:[下载链接](https://releases.hashicorp.com/vault/1.18.2/vault_1.18.2_windows_amd64.zip) 。
- 解压后将 vault.exe 添加到系统路径中。
Linux 环境
1. 下载 Vault:
wget https://releases.hashicorp.com/vault/1.18.2/vault_1.18.2_linux_amd64.zip
2. 解压并移动到 /usr/local/bin:
yum install -y unzip
unzip vault_1.18.2_linux_amd64.zip
sudo mv vault /usr/local/bin/3. 验证安装:
vault --version
4 启动 Vault
开发模式(适合测试)
- 启动开发模式:
vault server -dev- 设置环境变量:
export VAULT_ADDR='http://127.0.0.1:8200'- 使用开发模式的 Root Token 登录:
vault login
生产模式(独立模式)
1. 创建配置文件
mkdir /data/vault/data -p
vi/data/vault/config.hcl
# 启用 Vault 的 UI 界面
ui = true
# 禁用 mlock,这允许 Vault 将数据交换到磁盘,可能会降低安全性
# 在生产环境中建议设置为 true,除非你确定服务器支持 mlock
disable_mlock = false
# 配置存储后端为文件系统
# 数据将存储在 /data/vault/data 目录下
storage "file" {
path = "/data/vault/data"
}
# 配置监听器
# 监听地址为 0.0.0.0:8200,表示 Vault 将监听所有网络接口的 8200 端口
# 禁用 TLS,使用 HTTP
listener "tcp" {
address = "0.0.0.0:8200"
tls_disable = 1
}
# 配置 API 地址
# 客户端将通过这个地址与 Vault 通信
api_addr = "http://127.0.0.1"
# 设置日志级别为 info
log_level = "info"
2. 启动 Vault 服务:
vi /data/vault/start.sh
#!/bin/bash
# 设置环境变量
export VAULT_ADDR='http://127.0.0.1:8200'
# 启动 Vault 服务
start_vault() {
echo "Starting Vault server..."
nohup vault server -config=/data/vault/config.hcl > /data/vault/nohup.out 2>&1 &
sleep 3
echo "Vault server started."
ps -ef | grep vault
netstat -tnlp | grep vault
}
# 停止 Vault 服务
stop_vault() {
echo "Stopping Vault server..."
pkill -f "vault server"
sleep 2
echo "Vault server stopped."
}
# 重启 Vault 服务
restart_vault() {
echo "Restarting Vault server..."
stop_vault
start_vault
}
# 根据传入参数执行相应操作
case "$1" in
start)
start_vault
;;
stop)
stop_vault
;;
restart)
restart_vault
;;
*)
echo "Usage: $0 {start|stop|restart}"
exit 1
;
chmod +x /data/vault/start.sh
3. 初始化 Vault:
vault operator init -key-shares=3 -key-threshold=2输出
Unseal Key 1: xxxx
Unseal Key 2:xxxx
Unseal Key 3: xxx
Initial Root Token: xxxx
Vault initialized with 3 key shares and a key threshold of 2. Please securely
distribute the key shares printed above. When the Vault is re-sealed,
restarted, or stopped, you must supply at least 2 of these keys to unseal it
before it can start servicing requests.
Vault does not store the generated root key. Without at least 2 keys to
reconstruct the root key, Vault will remain permanently sealed!
It is possible to generate new unseal keys, provided you have a quorum of
existing unseal keys shares. See "vault operator rekey" for more information.记录生成的 Unseal Key 和 Root Token。
4.访问web页面根据提示输入第一个key和第三个key然后在输入token
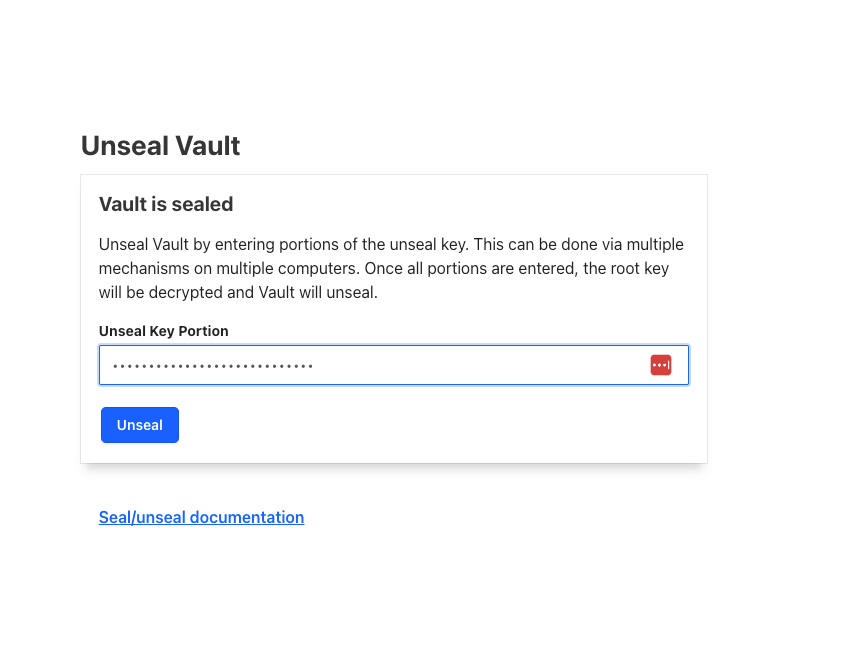
5. 基本操作
解封 Vault
- 使用生成的 Unseal Key 解封:
vault operator unseal输入任意 3 个 Unseal Key。
6.写入和读取秘密
1. 写入秘密:
vault write secret/hello value=world2. 读取秘密:
vault read secret/hello
7.创建策略
1. 创建策略文件 policy.hcl:
path "secret/hello" {
capabilities = ["create", "read", "update", "delete", "list"]
}2. 导入策略:
vault policy write my-policy policy.hcl
4. 高级配置(可选)
集群部署
- 配置文件中设置集群参数:
api_addr = "https://127.0.0.1:8200"
cluster_addr = "https://<Node-1-IP>:8201"
cluster_name = "vault-cluster"- 启动多个 Vault 实例并解封。
接入 LDAP
- 配置 LDAP 认证:
vault write -f auth/ldap/config \
url="ldap://ldap地址" \
userfilter:"(&(memberOf=cn=xxx,ou=xxx,ou=xxxx,dc=xxxx,dc=xxx)(uid={{.Username}}))"5. 审计日志
- 启用文件审计设备:
mkdir /data/vault/log/audit -p
vault audit enable file file_path=/data/vault/log/audit/vault-audit.log以上是 Vault 的基本安装、配置和使用方法。更多高级功能和详细配置可以参考 [HashiCorp 官方文档](https://learn.hashicorp.com/tutorials/vault/getting-started-deploy) 或相关社区资源。
- 感谢你赐予我前进的力量
赞赏者名单
因为你们的支持让我意识到写文章的价值🙏
作者编辑不易,如有转载请注明出处。完整转载来自https://wangairui.com 网站名称:猫扑linux
评论
匿名评论
隐私政策
你无需删除空行,直接评论以获取最佳展示效果


